Hardware and Software Concepts:Hardware Support for Operating Systems
Hardware Support for Operating Systems
Computer architectures contain features that perform operating system functions quickly in hardware to improve performance. They also provide features that enable the operating system to rigidly enforce protection, which improves the security and integrity of the system.
Processor
Most operating systems rely on processors to implement their protection mechanisms by preventing processes from accessing privileged instructions or accessing memory that has not been allocated to them. If processes attempt to violate a system’s protection mechanisms, the processor notifies the operating system so that it can respond. The processor also invokes the operating system to respond to signals from hardware devices.
User Mode, Kernel Mode and Privileged Instructions
Computer systems generally have several different execution modes.28 Varying the mode of a machine makes it possible to build more robust, fault-tolerant and secure systems. Normally, when the machine is operating in a particular mode, applications have access to only a subset of the machine’s instructions. For user applications, the subset of instructions the user may execute in user mode (also called the user state or problem state) precludes, for example, the direct execution of input/output instructions; a user application allowed to perform arbitrary input/output could, for exam- ple, dump the system’s master list of passwords, print the information of any other user or destroy the operating system. The operating system ordinarily executes with most trusted user status in kernel mode (also called the supervisor state); it has access to all the instructions in the machine’s instruction set. In kernel mode, a processor may execute privileged instructions and access resources to perform tasks on behalf of processes. Such a user mode/kernel mode dichotomy has been adequate for most modern computing systems. In highly secure systems, however, it is desirable to have more than two states to allow finer-grained protection. Multiple states allow access to be granted by the principle of least privilege—any particular user should be granted the least amount of privilege and access required to accomplish its designated tasks (see the Operating Systems Thinking feature, Principle of Least Privilege).
It is interesting that as computer architectures have evolved, the number of privileged instructions (i.e., those instructions not accessible in user mode) has tended to increase. This indicates a trend toward incorporating more operating systems functions in hardware.
Memory Protection and Management
Most processors provide mechanisms for memory protection and memory management. Memory protection, which prevents processes from accessing memory that has not been assigned to them (such as other users’ memory and the operating sys- tem’s memory), is implemented using processor registers that can be modified only by privileged instructions (see the Operating Systems Thinking feature, Protection). The processor checks the values of these registers to ensure that processes cannot access memory that has not been allocated to them. For example, in systems that do not use virtual memory, processes are allocated only a contiguous block of memory addresses. The system can prevent such processes from accessing memory locations that have not been allocated to them by providing bounds registers that specify the addresses of the beginning and end of a process’s allocated memory. Protection is enforced by determining whether a given address is within the allocated block. Most hardware protection operations are performed in parallel with the execution of program instructions, so they do not degrade performance.
Most processors also contain hardware that translates virtual addresses referenced by processes to corresponding addresses in main memory. Virtual memory systems allow programs to reference addresses that need not correspond to the lim-
Operating Systems Thinking
Principle of Least Privilege
Generally speaking, the principle of least privilege says that in any system, the various entities should be given only the capabilities that they need to accomplish their jobs but no more. The government employs this principle in awarding security clearances. You employ it when deciding who gets the extra keys to your home. Businesses employ it when giving employees access to critical and confidential information. Operating systems employ it in many areas.
ited set of real (or physical) addresses available in main memory.29 Using hardware, the operating system dynamically translates a process’s virtual addresses into physical addresses at runtime. Virtual memory systems allow processes to reference address spaces much larger than the number of addresses available in main memory, which allows programmers to create applications that are independent (for the most part) of the constraints of physical memory. Virtual memory also facilitates programming for timesharing systems, because processes need not be aware of the actual location of their data in main memory. Memory management and protection are discussed in detail in Chapters 9–11.
Interrupts and Exceptions
Processors inform the operating system of events such as program execution errors and changes in device status (e.g., a network packet has arrived or a disk I/O has completed). A processor can do so by repeatedly requesting the status of each device, a technique called polling. However, this can lead to significant execution overhead when polled devices have not changed status.
Instead, most devices send a signal called an interrupt to the processor when an event occurs. The operating system can respond to a change in device status by notifying processes that are waiting on such events. Exceptions are interrupts generated in response to errors, such as hardware failures, logic errors and protection violations (see the Anecdote, Origins of the Term “Glitch”). Instead of causing the
Operating Systems Thinking
Protection
The earliest computers had primitive operating systems capable of running only one job at a time. That changed rapidly as parallel processing capabilities were added to local systems and as distributed systems were developed in which parallel activities occur across networks of computers like the Internet. Operating systems must be concerned with various kinds of protection, especially when connected to the Internet.
The operating system and its data must be protected from being clobbered by errant user pro- grams, either accidentally or maliciously. User programs must be protected from clobbering one another. Such protection must be enforced on the local machine and it must be enforced among users and operating system components spread across computer networks. We study protection in many chapters of this book, especially in Chapter 9, Real Memory Organization and Management and Chapter 10, Virtual Memory Organization. We consider protection in the form of file access controls in Chapter 13, File and Database Systems. We discuss protection in general throughout the main portion of the book and then discuss it in the context of the Linux and Windows XP case studies in Chapters 20 and 21, respectively.
system to fail, a processor will typically invoke the operating system to determine how to respond. For example, the operating system may determine that the process causing the error should be terminated or that the system must be restarted. If the system must fail, the operating system can do so gracefully, reducing the amount of lost work. Processes can also register exception handlers with the operating system. When the operating system receives an exception of the corresponding type, it calls the process’s exception handler to respond. Interrupt mechanisms and exception handling are discussed in Section 3.4, Interrupts.
Self Review
1. What is the rationale for implementing multiple execution states?
2. How do exceptions differ from other types of interrupts?
Ans: 1) Multiple execution states provide protection by preventing most software from maliciously or accidentally damaging the system and accessing resources without authoriza- tion. These operations are restricted to kernel mode, which enables the operating system to execute privileged instructions. 2) Exceptions indicate that an error has occurred (e.g., divi- sion by zero or a protection violation) and invoke the operating system to determine how to respond. The operating system may then decide to do nothing or to terminate a process. If the operating system encounters a serious error that prevents it from executing properly, it may restart the computer.
Anecdote
Origins of the Term “Glitch”
There are a number of theories on the etymology of the computer term “glitch” which is typically used as a synonym for “bug.” Many suggest that it is derived from the Yiddish word “glitshen,” meaning “to slip.” Here is another take on this. In the mid 1960s during the height of the space program, one of the top computer vendors built the first on-board computer system. The morning of the launch, the computer vendor took out full-page ads in major publications around the world, proclaiming that its computer was safely guiding the astronauts on their mission. That day, the com-
puter failed, causing the space capsule to spin wildly out of con- trol, putting the astronauts' lives at risk. The next morning, one
of the major newspapers referred to this as the “Greatest Lemon in the Company's History!”
Lesson to operating systems designers: Always keep Murphy's Law in mind, “If something can go wrong, it will.” And don't forget the common addendum, “and at the most inopportune time.”
Timers and Clocks
An interval timer periodically generates an interrupt that causes a processor to invoke the operating system. Operating systems often use interval timers to prevent processes from monopolizing the processor. For example, the operating system may respond to the timer interrupt by removing the current process from the processor so that another can run. A time-of-day clock enables the computer to keep track of “wall clock time,” typically accurate to thousandths or millionths of a second. Some time-of-day clocks are battery powered, allowing them to tick even when there is no external power supplied to the computer. Such clocks provide a measure of continuity in a system; for example, when the operating system loads, it may read the time-of-day clock to determine the current time and date.
Self Review
1. How does an interval timer prevent one process from monopolizing a processor?
2. Processors often contain a counter that is incremented after each processor cycle, providing a measure of time accurate to nanoseconds. Compare and contrast this measure of time to that provided by the time-of-day clock.
Ans: 1) The interval timer generates interrupts periodically. The processor responds to each interrupt by invoking the operating system, which can then assign a different process to a processor. 2) A processor counter enables the system to determine with high precision how much time has passed between events, but does not maintain its information when the system is powered down. Because a time-of-day clock is battery powered, it is more appropriate for determining wall clock time. However, it measures time with coarser granularity than a processor counter.
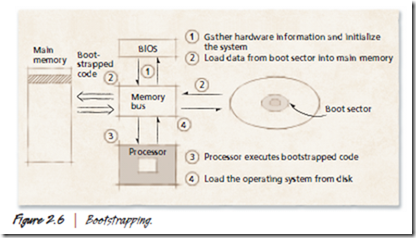
Bootstrapping
Before an operating system can begin to manage resources, it must be loaded into memory. When a computer system is powered up, the BIOS initializes the system hardware, then attempts to load instructions into main memory from a region of secondary storage (e.g., a floppy disk, hard disk or CD) called the boot sector, a technique called bootstrapping (Fig. 2.6). The processor is made to execute these instructions, which typically load operating system components into memory, initialize processor registers and prepare the system to run user applications.
In many systems, the BIOS can load an operating system from a predefined location on a limited number of devices (e.g., the boot sector of a hard disk or a compact disk). If the boot sector is not found on a supported device, the system will not load and the user will be unable to access any of the computer’s hardware. To enable greater functionality at boot time, the Intel Corporation has developed the Extensible Firmware Interface (EFI) as a replacement for the BIOS. EFI supports a shell through which users can directly access computer devices, and it incorporates device drivers to support access to hard drives and networks immediately after powering up the system.30
Self Review
1. How does EFI address the limitations of BIOS?
2. Why should the operating system prevent users from accessing the boot sector?
Ans: 1) A typical BIOS contains low-level instructions that provide limited functionality and restrict how software is initially loaded. EFI supports drivers and provides a shell, enabling a user to interact with a system and customize the way that the operating system is loaded. 2) If users could access the boot sector, they could accidentally or maliciously modify operating sys- tem code, making the system unusable or enabling an attacker to gain control of the system.
Plug and Play
Plug-and-play technology allows operating systems to configure and use newly installed hardware without user interaction. A plug-and-play hardware device
1. uniquely identifies itself to the operating system,
2. communicates with the operating system to indicate the resources and services it requires to function properly, and
3. identifies its corresponding driver and allows the operating system to use it to configure the device (e.g., assign the device to a DMA channel and allocate to the device a region of main memory).31
These features enable users to add hardware to a system and use the hardware immediately with proper operating system support.
As mobile computing devices become more popular, an increasing number of systems rely on batteries for power. Consequently, plug-and-play has evolved to include power management features that enable a system to dynamically adjust its power consumption to increase battery life. The Advanced Configuration and Power Interface (ACPI) defines a standard interface for operating systems to configure devices and manage their power consumption. All recent Windows operating systems support plug-and-play; Linux version 2.6 is compatible with many plug- and-play devices.32
Self Review
1. Why, do you suppose, is it necessary for a plug-and-play device to uniquely identify itself to the operating system?
2. Why is power management particularly important for mobile devices?
Ans: 1) Before an operating system can configure and make a device available to users, it must determine the resource needs that are unique to the device. 2) Mobile devices rely on battery power; managing a device’s power consumption can improve battery life.

Comments
Post a Comment