Introduction to Operating Systems:Operating System Components and Goals
Operating System Components and Goals
Computer systems have evolved from early systems containing no operating sys- tem, to multiprogramming machines, to timesharing machines, to personal computers and finally to truly distributed systems. As the demand for new features and improved efficiency grew and hardware changed, operating systems evolved to fill new roles. This section describes various core operating system components and explains several goals of operating systems.
Core Operating System Components
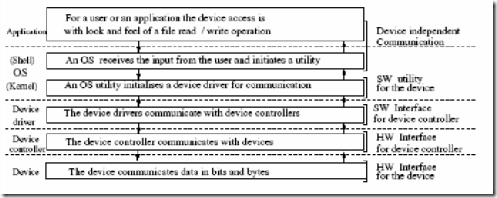
A user interacts with the operating system via one or more user applications. and often through a special application called a shell, or command interpreter.105 Most of today’s shells are implemented as text-based interfaces that enable the user to issue commands from a keyboard or as GUIs that allow the user to point and click and drag and drop icons to request services from the operating system (e.g., to open an application). For example, Microsoft Windows XP provides a GUI through which users can issue commands; alternatively, the user can open a command prompt window that accepts typed commands.
The software that contains the core components of the operating system is referred to as the kernel. Typical operating system core components include:
• the process scheduler, which determines when and for how long a process executes on a processor.
• the memory manager, which determines when and how memory is allocated to processes and what to do when main memory becomes full.
• the I/O manager, which services input and output requests from and to hardware devices, respectively.
• the interprocess communication (IPC) manager, which allows processes to communicate with one another.
• the file system manager, which organizes named collections of data on storage devices and provides an interface for accessing data on those devices.
Almost all modern operating systems support a multiprogrammed environment in which multiple applications can execute concurrently. One of the most fundamental responsibilities of an operating system is to determine which processor executes a process and for how long that process executes.
A program may contain several elements that share data and that can be executed concurrently. For example,a Web browser may contain separate components to read a Web page’s HTML, retrieve the page’s media (e.g., images, text and video) and render the page by laying out its content in the browser window. Such program components, which execute independently but perform their work in a common memory space, are called threads. Threads are discussed in Chapter 4, Thread Concepts.
Typically, many processes compete to use the processor. The process scheduler can base its decisions on several criteria, such as importance of a process, its estimated running time, or how long it has waited to obtain the processor. We discuss processor scheduling in Chapter 8, Processor Scheduling.
The memory manager allocates memory to the operating system and to pro- cesses. To ensure that processes to do not interfere with the operating system or with one another, the memory manager prevents each process from accessing memory that has not been allocated to it. Almost all of today’s operating systems sup- port virtual memory, as discussed in Chapters 10 and 11.
Another core function of the operating system is to manage the computer’s input/output (I/O) devices. Input devices include keyboards, mice, microphones and scanners; output devices include monitors, printers and speakers. Storage devices (e.g., hard disks, rewritable optical discs and tape) and network cards function as both input and output devices. When a process wishes to access an I/O device, it must issue a system call to the operating system. That system call is subsequently handled by a device driver, which is a software component that interacts directly with hardware, often containing device-specific commands and other instructions to perform the requested input/output operations.
Most computer systems can store data persistently (i.e., after the computer is turned off). Because main memory is often relatively small and loses its data when the power is turned off, persistent secondary storage devices are used, most com- monly hard disks. Disk I/O—one of the most common forms of I/O—occurs when a process requests access to information on a disk device.
Secondary storage, however, is much slower than processors and main memory. The disk scheduler component of an operating system is responsible for reordering disk I/O requests to maximize performance and minimize the amount of time a process waits for disk I/O. Redundant Array of Independent Disks (RAID) systems attempt to reduce the time a process waits for disk I/O by using multiple disks at once to service I/O requests. We discuss disk scheduling algorithms and RAID systems in Chapter 12, Disk Performance Optimization.
Operating systems use file systems to organize and efficiently access named collections of data called files located on storage devices. File system concepts are addressed in Chapter 13, File and Database Systems.
Often, processes (or threads) cooperate to accomplish a common goal. Thus, many operating systems provide interprocess communication (IPC) and synchronization mechanisms to simplify such concurrent programming. Interprocess communication enables processes to communicate via messages sent between the processes (and threads); synchronization provides structures that can be used to ensure that processes (and threads) share data properly. Processes and threads are discussed in Chapters 3 through 8.
Self Review
1. Which operating system components perform each of the following operations?
a. Write to disk.
b. Determine which process will run next.
c. Determine where in memory a new process should be placed.
d. Organize files on disk.
e. Enable one process to send data to another.
2. Why is it dangerous to allow users to perform read or write operations to any region of disk at will?
Ans: 1) a) I/O manager; b) processor scheduler; c) memory manager; d) file system man- ager; e) interprocess communication (IPC) manager.
2) It is dangerous because users could accidentally or maliciously overwrite critical data (such as operating system files) or read sensitive information (such as confidential documents) without authorization.
Operating System Goals
Users have come to expect certain characteristics of operating systems, such as:
• efficiency
• robustness
• scalability
• extensibility
• portability
• security
• interactivity
• usability
An efficient operating system achieves high throughput and low average turn- around time. Throughput measures the amount of work a processor can complete within a certain time period. Recall that one role of an operating system is to provide services to many applications. An efficient operating system minimizes the time spent providing these services (see the Operating Systems Thinking feature, Performance).
A robust operating system is fault tolerant and reliable—the system will not fail due to isolated application or hardware errors, and if it fails, it does so gracefully (i.e., by minimizing loss of work and by preventing damage to the system’s hard-
Operating Systems Thinking
Performance
One of the most important goals of an operating system is to maximize system performance. We are performance conscious in our everyday lives. We measure our cars’ gasoline mileage, we record various speed records, professors assign grades to students, employees receive performance evaluations from their employers, a corporate executive’s performance is measured by company profits, politicians’ performance is measured in frequent polls of their constituents and so on.
High performance is essential to successful operating systems.
However, performance is often “in the eye of the beholder”—there are many ways to classify operating system performance. For batch-processing systems, through- put is an important measure; for interactive timesharing systems, fast response times are more important.
Throughout the book we present many performance improvement techniques. For example, Chapter 8, Processor Scheduling, discusses allocating processor time to processes to improve system performance as measured by interactivity and throughput. Chapter 11, Virtual Memory Management, discusses allocating memory to processes to reduce their execution times. Chapter 12, Disk Performance Optimization, focuses on improving disk performance by reordering I/O requests. In Chapter 14, Performance and Processor Design, we discuss evaluating systems according to several important performance criteria. Chapters 20, and 21 discuss performance issues in the Linux and Windows XP operating systems, respectively.
ware). Such an operating system will provide services to each application unless the hardware it relies on fails.
A scalable operating system is able to use resources as they are added. If an operating system is not scalable, then it will quickly reach a point where additional resources will not be fully utilized. A scalable operating system can readily adjust its degree of multiprogramming. Scalability is a particularly important attribute of multiprocessor systems—as more processors are added to a system, ideally the processing capacity should increase in proportion to the number of processes, though, in practice, that does not happen. Multiprocessing is discussed in Chapter 15, Multi- processor Management.
An extensible operating system will adapt well to new technologies and pro- vide capabilities to extend the operating system to perform tasks beyond its original design.
A portable operating system is designed such that it can operate on many hardware configurations. Application portability is also important, because it is costly to develop applications, so the same application should run on a variety of hardware configurations to reduce development costs. The operating system is cru- cial to achieving this kind of portability.
A secure operating system prevents users and software from accessing services and resources without authorization. Protection refers to the mechanisms that implement the system’s security policy.
An interactive operating system allows applications to respond quickly to user actions, or events.A usable operating system is one that has the potential to serve a significant user base. These operating systems generally provide an easy-to-use user interface. Operating systems such as Linux, Windows XP and MacOS X are characterized as usable operating systems, because each supports a large set of applications and provides standard user interfaces. Many experimental and academic operating systems do not support a large number of applications or provide user- friendly interfaces and therefore are not considered to be usable.
Self Review
1. Which operating system goals correspond to each of the following characteristics?
a. Users cannot access services or information without proper authorization.
b. The operating system runs on a variety of hardware configurations.
c. System performance increases steadily when additional memory and processors are added.
d. The operating system supports devices that were not available at the time of its design.
e. Hardware failure does not necessarily cause the system to fail.
2. How does device driver support contribute to an operating system’s extensibility?
Ans:
1) a) security; b) portability; c) scalability; d) extensibility; e) robustness.
2) Device drivers enable developers to add support for hardware that did not exist when the operating system was designed. With each new type of device that is added to a system a corresponding device driver must be installed.

Comments
Post a Comment