Question on OS and Security.
Question Bank
9.1 What is vulnerability?
9.2 What is a security breach? Give two examples to illustrate a security breach.
9.3 What is a logic bomb? How it may manifest it self?
9.4 What precautions need be taken by a user in choosing password? Suggest a way to choose a good password.
9.5 What is authentication? Describe the authentication protocol you experience in using an ATM (automatic teller machines used by banks).
9.6 How does OS provide for security? What are the ways in which a systems' security may be compromised?
9.7 Differentiate between protection and security in the file system. .
9.8 Explain any two ways in which a password can be maintained.
9.9 Describe the process of encryption. What is public Key encryption?
9.10 Gives names of at least two agencies in the area of security standards and services.
9.11 Consider three sets of users, professor, TA and student. There exists a folder marks to which only professor can write into and student and TA can only read from. There exists another folder called course material which can be written to by professor and TA and students can only read from it. Use Access Control Lists to determine a security policy for this criteria.
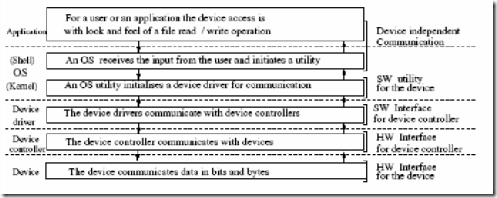
9.12 What are the different types of files? What are the tasks of the file management system? List some (at least two) file system related commands in UNIX? How does OS ensure security in file system?

Comments
Post a Comment